Locky goes offline (by design)
New Locky variant can encrypt files without directions from the ransomware’s CnC. That makes it tougher to block. But, this new variant may have the weakness that once someone has paid the ransom for their private key ID – it should be possible to reuse the same key for other victims with the same public key.

Locky ransomware now has a new offline mode that kicks in when all connections to the normal command & control centers fail.
The new variant – spotted July 12 – has a lot in common with teenagers that continue playing with their smartphones after a parent unplugs the WiFi router: Even though it looks like they have been disconnected, a workaround is discovered and the game goes on.
“Previously, a system administrator could block all CnC connections and keep Locky from encrypting any files on the system. Those days are over now,” said Moritz Kroll, malware specialist at Avira. “Locky has now reduced the chances for potential victims to avert an encryption disaster.”
When the new variant starts to work, the clock is running – and quickly. Locky runs through a set communication process where it first tries all CnCs from the configuration, then all CnCs from the DGA (12 per day). If that fails, it tries it again once with all CnCs, then it tries one CnC from the config again. If those all fail, it goes into offline encryption mode.
From initial Locky infection to starting offline encryption mode now takes between 1 and two minutes.
“While going through the CnCs, it made 3 delays for me, each lasting between 10-20 seconds. It’s not great for the admins trying to see the requests,” he said. “Although Locky is still trying to make connections and these can be observed, it will encrypt the files if this fails. So if an administrator notices such connections, there’s very little time left to shut down the computer before the data is damaged.”
Keys are different for offline victims
The new Locky has a different regime for generating ID numbers for its online and offline victims. In offline mode, the Locky cannot directly register a victim ID with the server and get a victim specific public key as is the usual practice. For those cases, it uses a public key which is part of the configuration and generates a special victim ID for the payment page.
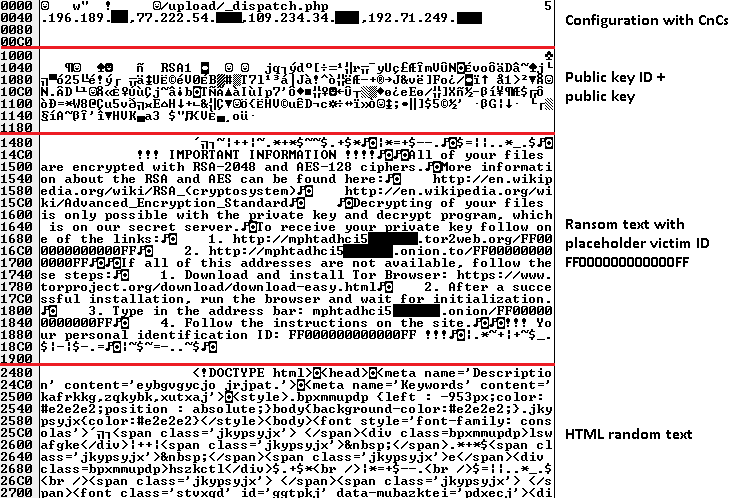
The public key for the new Locky is shared by all “offline victims” infected with samples that use the same configuration. This public key has an ID, so the server can eventually distinguish between public keys from different Locky configurations.
To be able to differentiate between the various offline victims and check whether they have already paid, Locky also generates a special victim ID which appears in the ransom note text.
The special victim ID is generated from:
- the first 6 hex digits of the normal victim ID which is based on a GUID from a harddisk partition
- the user default UI language
- the operating system version and type (server/non-server)
- whether it’s part of a domain controller (if so, the victim is probably part of a corporation, so the ransom demand can increase)
- the affiliate ID from the configuration (usually identifying which “channel” the malware was spread through)
- the public key ID from the configuration
Differentiating between the online and offline victims
To differentiate between normal victim IDs and special victim IDs, the new Locky uses a different encoding for the special victim IDs using a 32 character alphabet “YBNDRFG8EJKMCPQX0T1UWISZA345H769” to encode the ID instead of hex-digits “0123456789ABCDEF”. Based on this special victim ID, the Locky server can then extract thepublic key ID to deliver the correct private key to the victim.
Discounted ransom for discerning victims
As this private key will be shared with all other offline victims of the same Locky configuration, it creates several discounting potentials for victims. “Theoretically, if a company with a domain controller is hit by the new Locky and sees a non-hexdigit ID like “BSYA47W0NGXSWFJ9”, it might be cheaper to generate a victim ID with the same public key ID but without saying it’s a corporate computer,” Kroll pointed out. “The private key contained in the decrypter for the non-corporate public key ‘should’ also work for the corporate computer – and for all other victims with the same public key. Of course, it is better to take precautions, have a data backup policy, and not be hit at all.”
Reference sample: SHA25601aa8c430a9653cc4ae0574e151658bde36fe59e57d3489e4216e4a0ef402170



